A new Thomson Reuters Labs data visualization shows the frequency, range and scope of state-attributed cyberattacks increasing.
Private sector enterprises in diverse sectors including entertainment, finance, health-care, education, and telecommunications – not just government and military organizations – are being increasingly targeted by states or state-sponsored entities in cyber-attacks. The ubiquity of reliance on the Internet for doing business, combined with lax cybersecurity processes, has created the opportunity for state actors to achieve foreign policy objectives via cyber-attack, some of which tactically involve the targeting of private enterprise. The Digital and Cyberspace Policy program at the Council on Foreign Relations have aggregated nearly three hundred publicly available entries of state-attributed cyber incidents from credible sources, including Reuters News and government reports, about half of which (142 of 288) involve private sector targets.
It is difficult to compare these numbers with non-state sponsored attacks because “state-sponsored incidents generally have the most accurate and comprehensive reporting,” while attacks by non-state actors are less comprehensively reported, according to the Council.
Attacks on private entities include the 2018 hacking of German energy firms, a 2017 phishing campaign to steal network access credentials at U.S. power plants and other plants, the well-publicized 2016 and 2015 disruptions to Ukrainian power grids — the first suspected large-scale power outages enabled by cyberattack, and the 2014 targeting of AMC Theaters and Sony Pictures. These attacks target private entities for strategic reasons rather than necessarily for economic gain, although blackmail and cyber ransoms can play a part as well.
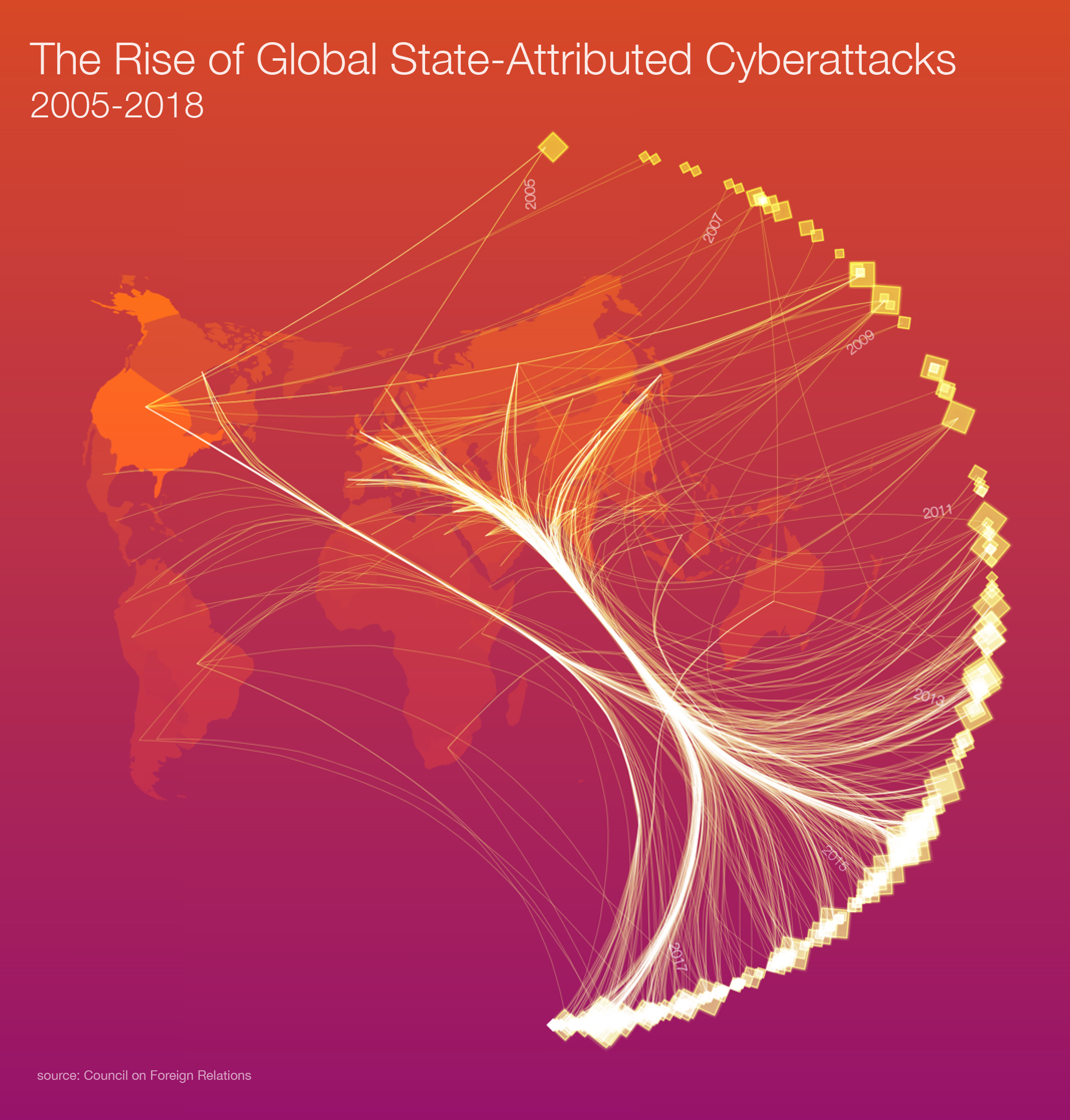
Thomson Reuters Labs created a visualization of this state-attributed cyberattack dataset, highlighting the size of the effect per attack, based on the number of targets affected as part of a collaboration with the World Economic Forum for Our Shared Digital Future, a new expansive report on shaping the future of our (digital) world. We have not represented the alleged sources of the attacks, which in some cases remain disputed. As our graphic shows, the frequency, range and scope of these attacks is increasing.
The United States [65] is the most commonly occurring target in this dataset, followed by United Kingdom [34], Germany [30], India [28], South Korea [27], China, Russia, Japan, Iran, and Israel, in descending order of the top ten targets.
The most common non-state victims of state sponsored attacks in the dataset are United Nations [3], Yahoo [3], the Asia-Pacific Economic Cooperation [2], and Bank of America [2].
According to the Council’s data, 22 countries are suspected of sponsoring cyber operations, including the United States. State retribution for these attacks, including those on private business, are on the rise in the form of state sanctions and indictments of suspects.
Attributing attacks to specific entities is difficult, and methodologies for doing so reliably and systematically are evolving. As a recent report states, “most sophisticated and exhaustive approaches to attribution are often outside the means of most companies, and from the perspective of the government or its intelligence organizations, is usually classified or sensitive.” This leaves private enterprise in a difficult position when it is targeted by state actors. They may fail to anticipate being targeted and lack the ability to respond when they are.
State-sponsored cyber-attacks are an emerging and significant risk to private enterprise that will increasingly challenge those sectors of the business world that provide convenient targets for settling geopolitical grievances.
Learn more
Access the full report, Our Shared Digital Futures, which addresses the need for shared goals and coordinated action to shape an inclusive, sustainable, digital future.
View the other articles in this series:






